|
Model
|
Restricted License1
|
Unrestricted License
|
||||
|---|---|---|---|---|---|---|
|
Total Interfaces
|
Physical Interfaces
|
Logical Interfaces
|
Total Interfaces
|
Physical Interfaces
|
Logical Interfaces
|
|
|
PIX 5012 |
NA |
NA |
NA |
2 |
2 10/100 |
Not supported |
|
PIX 506/506E |
NA |
NA |
NA |
4 |
2 10/100 |
2 |
|
PIX 515/515E |
5 |
3 x 10/100 |
3 |
10 |
6 x 10/100 |
8 |
|
PIX 5203 |
NA |
NA |
NA |
12 |
6 |
10 |
|
PIX 525 |
8 |
6 x 10/100 or |
6 |
12 |
8 x 10/100 or |
10 |
|
PIX 535 |
10 |
8 x 10/100 or |
8 |
24 |
10 x
10/100 or |
22 |
| 1
PIX 501 and PIX 506/506E do not support
Restricted/Unrestricted licenses. 2 Inside interface of the PIX 501 connects to an integrated 4-port switch. 3 PIX 520 supports a connection license and the number of interfaces does not vary with the connection license. |
Note: To determine the maximum number of logical interfaces that you can use, subtract the number of physical interfaces in use on your PIX Firewall from the number of total interfaces. A PIX must always have a minimum of 2 interfaces (its not much use with fewer ;-) ), so - for example - a PIX 525 can have a total of 12 interfaces, will have a minimum of 2 physical interfaces and can therefore have a maximum of 10 logical interfaces.
| PIX Model |
Cleartext Throughput |
Concurrent Sessions |
3DES VPN Throughput |
Concurrent VPN Tunnels |
|---|---|---|---|---|
| 501 |
60Mb/s |
7500 |
3Mb/s |
10 |
| 506E |
100Mb/s |
25,000 |
17Mb/s |
25 |
| 515/515E Restricted |
188Mb/s |
130,000 |
~24Mb/s
(estimate) (no VAC option) |
2000 |
| 515/515E Unrestricted |
140Mb/s with VAC+ 63Mb/s with VAC |
|||
| 525 Restricted |
330Mb/s |
280,000 |
35Mb/s
(estimate) (no VAC option) |
2000 |
| 525 Unrestricted |
155Mb/s
with VAC+ 72Mb/s with VAC |
|||
| 535 Restricted |
1.7Gb/s |
500,000 |
? (no VAC option) |
2000 |
| 535 Unrestricted |
440Mb/s with VAC+ 100Mb/s with VAC |
| interface ethernet1 100full | Set speed and duplex on physical
interface |
| interface ethernet1 vlan18 physical | Declare the VLAN for traffic on
the "physical" interface. You should avoid using VLAN 1 for this
(VLAN 1 is the default, untagged, VLAN on Cisco switches, which causes
some security problems) |
| interface ethernet1 vlan19 logical interface ethernet1 vlan20 logical linterface ethernet1 vlan22 logical |
Declare
additional VLANs on this interface |
| nameif ethernet1 inside
security100 nameif vlan19 DMZ1 security10 nameif vlan20 DMZ2 security0 nameif vlan22 DMZ3 security0 |
Name all interfaces (physical
and logical) and assign security levels to them |
| ip address inside 192.168.1.1
255.255.255.0 ip address DMZ1 192.168.2.1 255.255.255.0 ip address DMZ2 192.168.3.1 255.255.255.0 ip address DMZ3 192.168.4.1 255.255.255.0 |
Assign IP addresses to all
interfaces (phyiscal and logical) in the normal way |
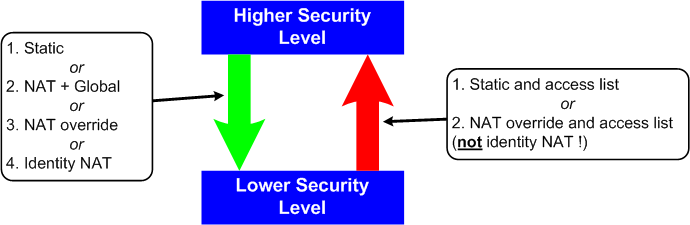
The diagram below summarises the golden rules for configuring NAT on a PIX. The arrow indicates traffic direction and the text box indicates the configuration elements required to allow traffic to flow in that direction

It is often desirable to disable NAT completely. There are three main ways to achieve this which differ in subtle but crucially important ways:-
nat (interface) 0 network netmask
This command declares that traffic from network/netmask originating on interface interface should be NATed to itself for traffic going to a lower security level. Note that this command has no effect on traffic going from a lower security level to interface (i.e. you would still need a static entry).
nat (interface) 0 access-list access-list-name
This command declares that traffic originating on interface interface matching access-list-name and going to an interface with a lower security level should not be subject to NAT. This also works for traffic going in the other direction (i.e. from a lower security level interface to interface interface. This means that you do not need static commands to facilitate lower-to-higher traffic matching access-list-name
It is normal (although not necessary) to use this form of the NAT command to disable NAT for traffic on site-to-site IPSec VPNs
GOTCHA - You can't use "deny" clauses in this ACL the way you might intuitively imagine that you could. For example, lets say you have an inside network of 192.168.1.0/255.255.255.0 and an outside network of 192.168.2.0/255.255.255.0. You want to disable NAT for all traffic between these two networks except for traffic to host 192.168.2.1 which should still be subject to NAT.
You might be tempted to do this:-
nat 0 (inside) access-list NoNat access-list NoNat deny 192.168.1.0 255.255.255.0 host 192.168.2.1 access-list NoNat permit 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0 : :
The first line of the ACL says that traffic to 192.168.2.1 should not be included in the exemption (i.e. should be subject to NAT). The second line exempts all other traffic from NAT.
As intuitive as it looks, it doesn't work. You can't use "deny" clauses in ACLs used for NAT exemption. If you try, the PIX behaves in strange ways and complains about missing routes.
static (higher,lower) address address [netmask]
This command statically NATs traffic matching address/netmask (netmask defaults to 255.255.255.255) originating on interface higher and going to interface lower should be NATed to itself.
If you've got lots of interfaces on the PIX, this will probably be a very unwieldy way to disable NAT between them (because you will need lots of these static commands for different "pairs" of interfaces)
